 As Enterprise networking moves into a new era headlined by SDN (software defined networking), automation and intent at the core of most modern next generation architectures, the security environment is keeping pace and is seeing the generational overhaul occur in cohesion with the network. Security architectures are now seen as defence in depth eco-systems built with layers and designed to interact and integrate with one another as they entwine with the network infrastructure in order to share information freely in an effort to reduce the mean time to detection of bad actors and malicious transactions within the domain.
As Enterprise networking moves into a new era headlined by SDN (software defined networking), automation and intent at the core of most modern next generation architectures, the security environment is keeping pace and is seeing the generational overhaul occur in cohesion with the network. Security architectures are now seen as defence in depth eco-systems built with layers and designed to interact and integrate with one another as they entwine with the network infrastructure in order to share information freely in an effort to reduce the mean time to detection of bad actors and malicious transactions within the domain.
One of the leading marketed security strategies currently is that of “Zero Trust”, which is truly a buzz word in the industry with most vendors offering their own twist on what Zero Trust is and what it should be. The reality is that whilst it can be easy to get caught up in the marketing, Zero Trust is not a product, it is not a set of products and it is not a specific solution. The preceding elements can absolutely make up the components of a Zero Trust architecture, but “Zero Trust” is more than a set of products or a new solution from a specific vendor. Zero Trust is a methodology. It is an alteration in the mindset of individuals who are responsible for the security systems of a given organisation. For example, architects, engineers, analysts, management all need to onboard the approach for Zero Trust to be achieved in any environment.
What is Zero Trust?
So, if Zero Trust is a methodology and not a specific solution, what is the methodology? Simply put, the core concept is to trust nothing or no one to access any resources, internal or external to your organisation by default. We do not let them connect until an identity has been provided. An identity could be a user, or/and a device. Once they have authenticated and been authorised/verified they will be permitted to access the specific resources. “Specific” is a key word, as the concept of Zero Trust is that an authenticated identity on the network should only be permitted access to the appropriate resources required for the user/device to perform their job or for the function to be served, and this is enforceable policy based on the user or device identity, location, time of day, posture etc. A simple example of a Zero Trust policy is that you may have a corporate finance user permitted access to finance applications on their corporate laptop, however if that user is seen connecting with a personal IPAD, the permissions should be amended for that user based on the fact they are not accessing the domain with a corporate device. In this scenario the user may be granted staff internet only access and access to the internal corporate intraweb. The beauty of this approach is that security policy is dynamic and can change based on real time connection events. The Zero Trust approach can also be applied on all medias within an organisation such as wired, wireless and VPN, with a consistent experience for users and their privileges regardless of how they connect.
The Zero Trust approach differs from the traditional “castle-and-moat” concept where security architectures would fortify centralised resources from external penetration with firewalls and ACLs, yet would consider internal users as trusted, and permit access to all resources if you were connected behind the perimeter firewalls. This legacy approach is no longer fit for purpose in most enterprise environments and cannot scale from a secure policy perspective to support the growing connectivity demands placed on the network from the likes of mobile devices, IoT solutions, etc. In addition, most companies no longer house their data in one central location based on the emergence of cloud technologies, IaaS and SaaS applications, making the castle-and-moat architecture ineffective. The Zero Trust model is built to allow scale, ease of management, and offer more intelligence into the security policy which will be defined centrally by the company. The adoption of this methodology is a big change with varying degrees of complexity dependant on the organisation. To transition from an open access environment to a Zero Trust closed domain is not a quick process and is something that should be migrated too, at a pace that is comfortable for the business in question. Companies will have differing requirements, concerns and challenges to overcome, yet all should aspire to adopt the modern concept in time based on the many advantages it brings to a company’s security posture. Security professionals should be shifting their approach with the next generation of security architectures by questioning specifically “who/what needs access to what?”, as opposed to “what do I need to defend?”
What Are Zero Trusts core components?
A Zero Trust approach sees best practises bound together to offer greater fortification to all environments. This includes multiple layers of segmentation such as creating virtual networks to segment devices types, such as IoT IP cameras, HVAC systems, IP Lighting sensors etc. These types of devices would be segmented from corporate devices, which in turn would be segmented from PCI or HIPPA etc environments ensuring compliancy is upheld. This process is the practice of breaking up security perimeters into small zones to maintain separate access for separate parts of the network.
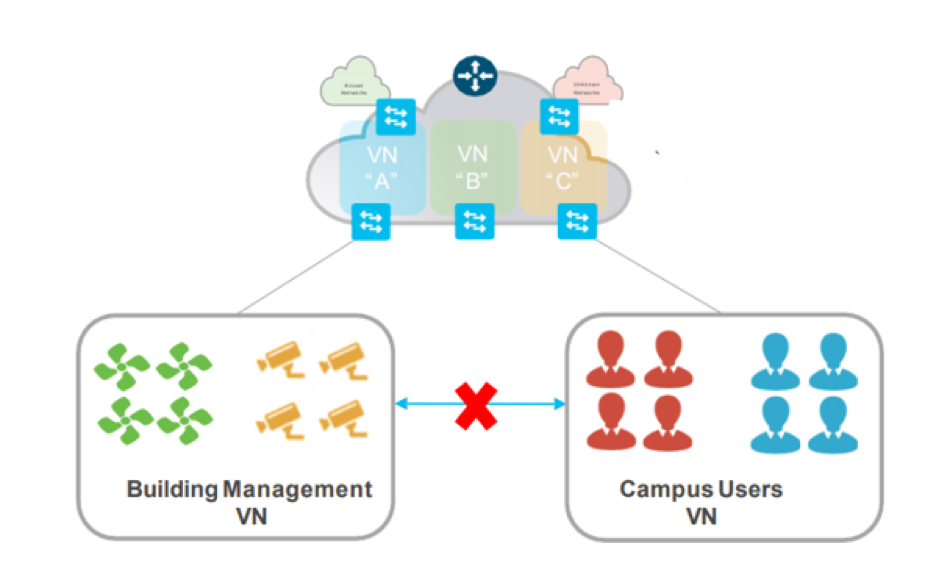
In addition, micro segmentation can be overlayed to segment further within the forementioned virtual networks. This for example allows corporate assets to be housed in the same virtual network container, yet still be segmented from communication with one another. For example, HR resources and finance resources could both be located in the same virtual network. However, through the use of micro segmentation policy could enforce access to those resources based on who you are and the device you connect from, ensuring only HR users can access HR resources, and denying Finance users from that access. The below visual depicts CCTV cameras and HVAC systems in the same virtual network yet based on policy cannot communicate with one another.
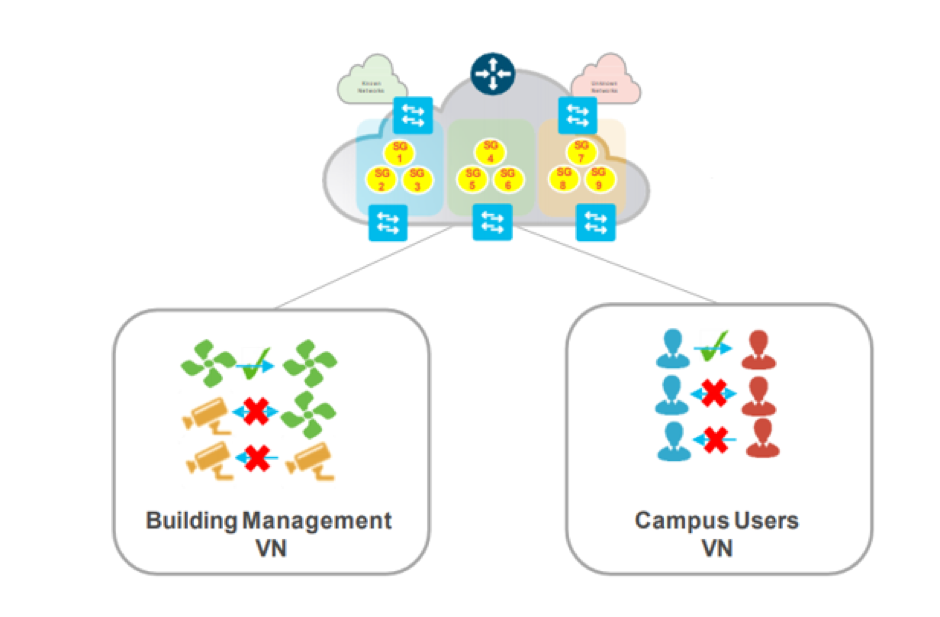
This type of segmentation protects environments form lateral movement across the network. Most attackers will look to compromise the easy targets such as IP cameras, then from that foothold pivot throughout the network attempting to compromise anything they can. This Zero Trust architecture prevents that lateral movement minimising the attack surface and descoping a number of risks when considering the types of devices connecting to the network.
Multi-factor authentication (MFA) is also a core value of Zero Trust security. MFA simply means requiring more than one piece of evidence to authenticate a user; just entering a password is not enough to gain access. This authentication method can be applied to enterprise cloud applications, and internal applications offering consistency for the end users. A commonly seen application of MFA is the 2-factor authorization (2FA) used on popular online platforms like Facebook and Google. In addition to entering a password, users who enable 2FA for these services must also enter a code sent to another device, such as a mobile phone, thus providing two pieces of evidence that they are who they claim to be.
Devices will be monitored within a Zero Trust architecture and will adhere to strict controls. No corporate devices will typically not be permitted from communicating with corporate assets unless a BYOD policy permits such transactions. This type of control protects the environment from potential malicious code accessing the network from untrusted devices. Device posture can be gleaned in a Zero Trust environment and dynamic decisions can be taken as to whether the device in question should be permitted onto the network. This can be interrogations such as anti-malware status, OS updates status, Browser version, USB connected, currently running applications etc. Again, these strategies are used to protect the network from infection, from untrusted devices whether they be corporate or personal.
Access restrictions and edge protection are both elements to add to a Zero Trust architecture regardless of the connection method such as Wireless, Wired, VPN, or browser to the cloud. A Zero Trust architecture should deny the user or traffic flow at source if they do not meet the access and authorisation requirements. This may be to deny access to the cloud application or the use of a Cloud broker to restrict the user on a cloud application. In addition, this could take the form of restricting wireless traffic or wired traffic at the point of ingress or dropping unpermitted traffic on a VPN connection when on premise. The whole infrastructure should be capable of enforcing policy at the points of ingress to restrict any unpermitted traffic flows traversing the network before being dropped.
In summary Zero Trust is a concept that is currently sweeping through the industry as organisations look to refresh existing infrastructures and adopt a more modern stance on enterprise system security in an effort to keep pace with the ever-present sophisticated attacks of today’s world and mitigate as much risk as possible using architecture to meet those needs. It is not a one size fits all, and it has a number of different core components. Ultimately Zero Trust needs to be bought into by the stakeholders and strategized, with a roadmap to achieving the end goal. Most journeys will be different and should be tailored to the organisation in question.
Find out how Zero Trust can transform your network security.
Contact us today to schedule a meeting and to find out if Zero Trust is right for you.
enquiries@isn.co.uk or 0203 239 2476




